Serving tech enthusiasts for over 25 years.
TechSpot means tech analysis and advice you can trust.
Facepalm: Microsoft recently released its latest batch of monthly security updates for Windows and other software products. However, a bug fix designed to address a Secure Boot vulnerability discovered two years ago is causing issues for Linux users, rendering dual-boot configurations unbootable.
Microsoft's Patch Tuesday for August 2024 includes a fix for a security vulnerability in the Grub2 boot loader, which is used by many Linux operating systems. Tracked as CVE-2022-2601, this flaw, discovered in 2022, could lead to an out-of-bounds write with a potential bypass of Secure Boot protection.
The Grub2 boot loader provides compatibility with the Secure Boot technology on PCs running Linux systems. After installing the new patch, Windows applies a Secure Boot Advanced Targeting (SBAT) policy to block vulnerable Linux boot loaders that could compromise OS security.
Microsoft explained that the SBAT value would not be applied to dual-boot systems with both Windows and Linux on the boot drive, so the patch was expected not to impact these systems. However, many users with dual-boot configurations have reported that the CVE-2022-2601 update still rendered booting into a Linux OS impossible.
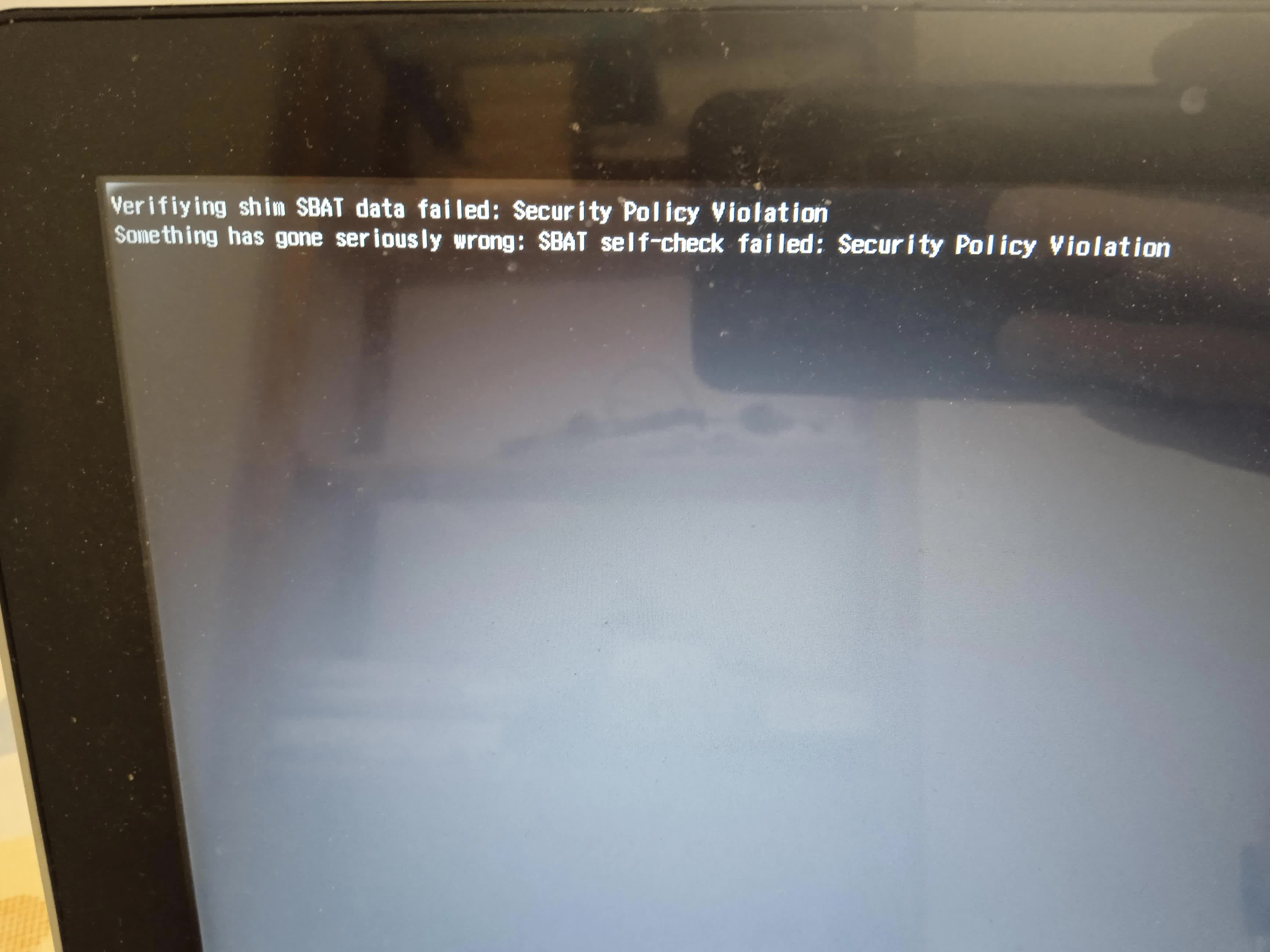
The issue appears to affect various Linux distributions, including popular ones such as Ubuntu, Linux Mint, Zorin OS, Puppy Linux, and others. Affected systems typically display a "Security Policy Violation" error at boot, indicating a failed check on "shim SBAT data." Boot problems have been reported on both dual-boot systems and on Windows devices running Linux from an ISO image, USB drive, or optical media.
Microsoft's bulletin noted that only older Linux distros' ISOs were expected to experience boot issues following the CVE-2022-2601 patch. However, users with systems released in 2024 also seem to be affected. The only reliable way to restore a bootable state appears to be disabling Secure Boot entirely. Alternatively, users can follow the steps to remove the SBAT policy introduced by Microsoft this past week.
Secure Boot has long been a point of contention in the Linux community. Designed to protect Windows PCs from rootkits and sophisticated attacks, this technology has introduced significant compatibility issues with Linux, while offering minimal protection against real-world malware or for the Windows ecosystem as a whole.